Unbreakable Code: Emerging Trends in Computer Security

Unbreakable Code: Emerging Trends in Computer Security
Computer security, also known as cybersecurity or information technology security, is the practice of protecting computer systems, networks, and data from digital attacks, unauthorized access, theft, damage, disruption, or misdirection.
It involves a combination of technologies, processes, and practices designed to safeguard information and ensure the confidentiality, integrity, and availability of data.
Concepts and techniques for safeguarding confidential data in computer systems are included in computer security. A policy that controls access to protected resources is where computer security begins. The means for implementing these policies are the main emphasis of technology.

Possible Attacks and Threats
Computer security threats and attacks are ever-evolving challenges in the digital age, targeting vulnerabilities in systems and networks. Common threats include malware, such as viruses, worms, and trojans, which can corrupt or steal data, and ransomware, which locks users out of their systems until a ransom is paid. Phishing attacks trick individuals into revealing sensitive information, while denial-of-service (DoS) attacks overwhelm systems to make them unavailable. Advanced persistent threats (APTs) involve prolonged, targeted cyber espionage, often aimed at stealing intellectual property or state secrets.
Additionally, insider threats, where employees misuse access, and zero-day exploits, which target previously unknown vulnerabilities, pose significant risks. Effective cybersecurity measures are essential to protect against these diverse and sophisticated threats.
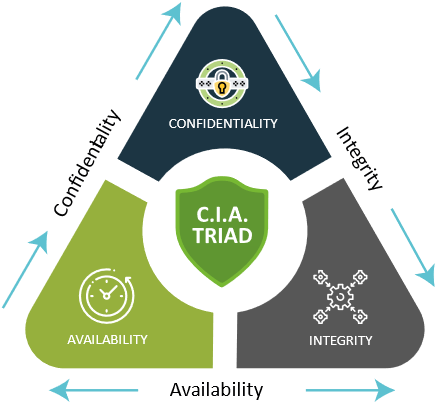
Information Security : CIA
Information security is crucial in today's digital landscape as it protects sensitive data from unauthorized access, breaches, and cyber threats. By implementing robust security measures, organizations can safeguard their intellectual property, customer information, and financial data, maintaining trust and credibility with clients and stakeholders.Effective information security also ensures compliance with legal and regulatory requirements, avoiding fines and legal repercussions. Moreover, it enhances operational efficiency by preventing disruptions caused by cyber-attacks, allowing businesses to focus on growth and innovation. In essence, information security is vital for maintaining the integrity, confidentiality, and availability of critical information, ultimately contributing to the overall success and resilience of an organization.
The trinity of "great" information security comprises three fundamental principles: Three key principles are involved in handling data: confidentiality, which aims to stop purposeful or unauthorized disclosure; integrity, which states that data is a system and should not be altered; availability, which limits access to the data to specific staff members.
Data breaches, thefts, and cyberattacks are happening more often. When a firm has inadequate security practices, data breaches occur. Thus, there is a compromise of user data. An organization should use the CIA trinity to improve its cybersecurity policy to solve these issues.
Is Computer Security is Important?
Yes, computer security is extremely important. Here are some key reasons why:- Protection of Personal Information: Ensuring that personal data such as social security numbers, financial information, and other sensitive details are secure is crucial to prevent identity theft and fraud.
- Business Continuity: For businesses, protecting data and systems is essential to maintain operations and avoid disruptions that could lead to significant financial losses and damage to reputation.
- Protection from Cyber Attacks: Cyber attacks, such as malware, ransomware, and phishing, can compromise systems, steal sensitive information, and cause significant harm. Robust security measures help protect against these threats.
- Legal and Regulatory Compliance: Many industries have regulations and legal requirements regarding data protection. Non-compliance can result in hefty fines and legal repercussions.
- Intellectual Property Protection: For companies, securing intellectual property like proprietary software, designs, and trade secrets is essential to maintain competitive advantage.
- Privacy: Maintaining the privacy of communications and data is a fundamental right and essential for trust in digital interactions.
- National Security: For governments and critical infrastructure, robust computer security is essential to protect against espionage, sabotage, and other forms of cyber warfare.
Professional Diploma in IT Support
- Encryption and Cryptography: Basics of encryption, including symmetric and asymmetric cryptography, and how they are used to protect data.
- Authentication and Access Control: Methods for verifying identities and managing access to resources, including passwords, biometrics, and multi-factor authentication.
- Emerging Technologies and Trends: Keeping up with the latest trends and technologies in computer security, such as AI in cybersecurity, blockchain, and quantum computing security.
- Security Tools and Software: Learning about various tools and software used in the industry for security purposes, such as antivirus programs, encryption tools, and security information and event management (SIEM) systems.
- User Education and Awareness: Strategies for educating and training users on security best practices to minimize human-related security risks.
By gaining expertise in these areas, IT support professionals can significantly contribute to an organization’s security posture, ensuring robust protection against cyber threats.
Conclusion
In conclusion, IT support plays an indispensable role in Computer Security.Computer security is crucial in today's digital age as it protects sensitive information from unauthorized access, theft, and damage. With the increasing reliance on computers and the internet for personal, financial, and business activities, the risk of cyber threats has grown significantly. Effective security measures ensure the confidentiality, integrity, and availability of data, safeguarding against cyberattacks such as hacking, malware, and phishing. Moreover, robust computer security helps maintain trust and compliance with legal and regulatory requirements, preventing financial losses and reputational damage. As cyber threats continue to evolve, investing in advanced security protocols and practices is essential to protect critical assets and maintain operational continuity.

Aug 12,2024
